Resilient Identity Access for Disconnected and DDIL Environments
Credenti AlwaysON ensures users can always sign in — even when the primary identity provider is down. Its orchestration engine dynamically shifts authentication across available sources, maintaining Zero Trust enforcement at the edge.
Ideal for enterprises and organizations needing high availability across cloud and on-prem identity systems.
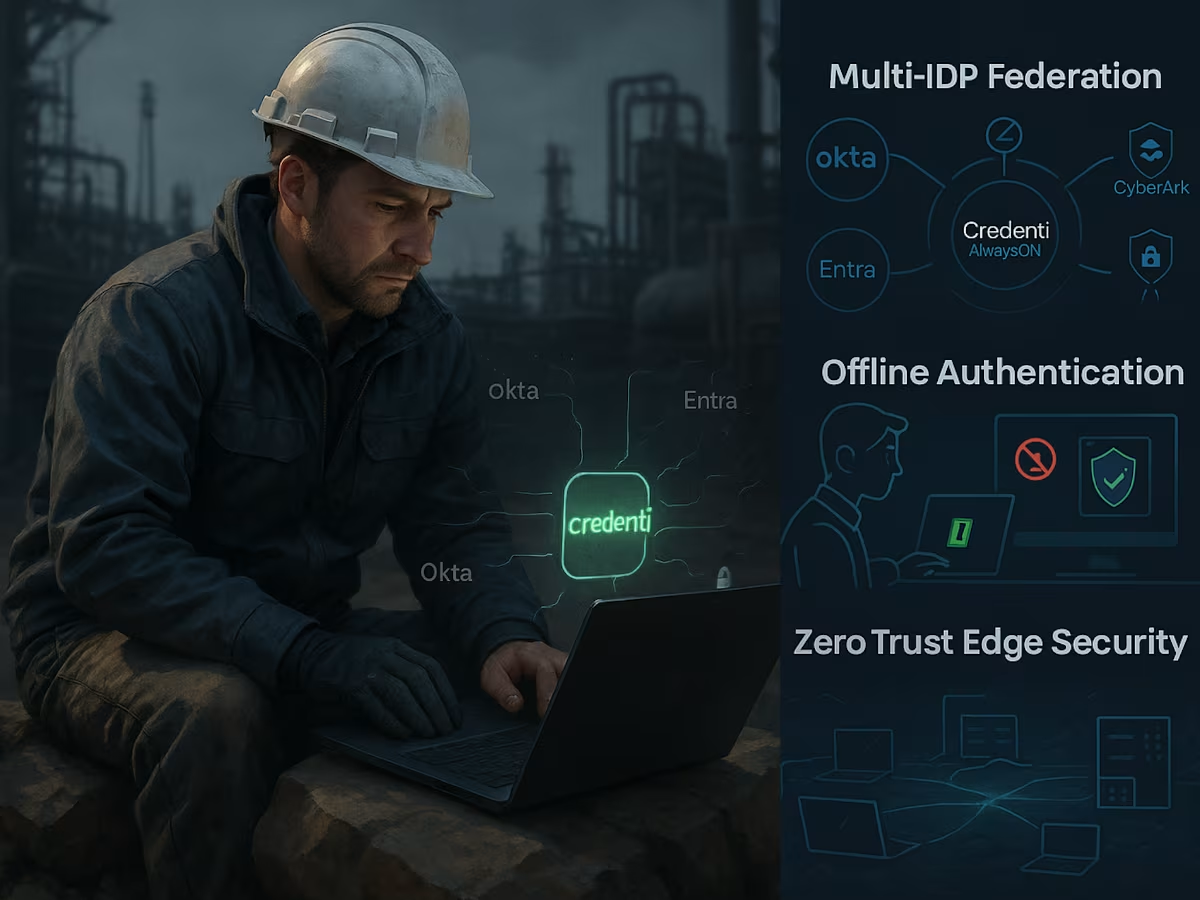
High Availability Identity Orchestration & Multi-IdP Federation
The Credenti AlwaysON platform delivers resilient, passwordless access in Denied, Disrupted, Intermittent, or Limited (DDIL) connectivity environments. From tactical edge deployments to offline industrial systems, Credenti ensures Zero Trust access with capabilities like redundant identity enforcement, unified sign-on across machines and applications, multi-vendor IdP integration, and automatic failover between identity providers — even without internet connectivity.
CAC Card, PIV-I, Passkey, and RFID Badge
Enable secure, passwordless authentication to unlock workstations or access the edge-deployed portal, even in air-gapped or DDIL environments.
Seamless Integration with Leading Identity Providers
Credenti AlwaysON works in tandem with platforms like Okta and Microsoft Entra, extending your existing identity infrastructure to even the most disconnected or restricted environments.
High Availability Identity Orchestration & Multi-IdP Federation
Even when cloud identity providers are unavailable, Credenti AlwaysON ensures users can securely authenticate and access critical systems. Its high availability orchestration engine maintains authentication, authorization, and access control without disruption — sourcing users from both cloud directories and on-prem Active Directory for unified policy enforcement across environments.
Built for DDIL Environments
Credenti AlwaysON is designed to support disconnected, disrupted, intermittent, and limited connectivity conditions. It can scale from small remote outposts to thousands of edge devices and continues to operate independently when networks fail. Authentication, access control, and policy enforcement continue seamlessly — ensuring mission continuity in any environment.
Smart Offline Authentication
Users can authenticate locally through Active Directory or any edge-available directory when offline. The platform supports seamless SSO for both on-prem and cloud applications. It integrates with Okta, Entra, and supports CAC/PIV cards, FIDO2, TOTP, and other MFA methods. User lifecycle is managed via SCIM-based provisioning for consistency across environments.
Edge-Deployed Access Portal
This localized portal runs directly at the edge, ensuring access continuity even in disconnected conditions. It dynamically displays cloud and local applications based on current connectivity, reconnects to cloud IDPs automatically, and synchronizes credentials and policies with central identity platforms.
Autonomous & Resilient Operations
Credenti AlwaysON operates independently at the edge, caching user data, logs, and app states locally. It queues offline requests and executes them automatically once reconnected — preserving continuity, auditability, and operational control in disconnected environments.
Edge-Based Policy Enforcement
Credenti enforces authentication and access policies locally on the device. Role-based access control, device trust evaluations, and admin rules are processed without relying on a constant connection. This local-first model ensures uninterrupted enforcement, even across rugged, unreliable, or isolated deployments.
Deployable Anywhere — Including the Tactical Edge
Credenti AlwaysON can operate in the harshest, most isolated environments — from mobile command centers to rugged OT environments — with full enforcement of Zero Trust principles, even offline.
What is the Tactical Edge? The tactical edge refers to locations at the farthest points of operation — where real-time connectivity is often unavailable or unreliable. These include battlefields, disaster response zones, remote field operations, and ruggedized industrial deployments. At the tactical edge, decision-making, authentication, and policy enforcement must happen locally and autonomously. Credenti AlwaysON is purpose-built for these scenarios — ensuring secure, passwordless access and policy control, regardless of the network status.

Consistent Control — Online or Offline
Whether online or disconnected, Credenti AlwaysON enforces authentication, access control, admin policies, and audit logging — all locally, without compromise.
Frequently Asked Questions
How does Credenti AlwaysON help enterprise organizations?
It protects against outages, broken configurations, or internet disruptions by automatically failing over to an on-premises Credenti IdP. Users can continue accessing mission-critical applications without interruption until connectivity or cloud identity services are restored.
Can Credenti AlwaysON be deployed in air-gapped or DDIL environments?
Yes. The platform is designed for mission-critical deployments with no internet dependency, enabling full authentication and access control even when isolated.
Does it support integration with existing identity providers?
Absolutely. Credenti AlwaysON integrates with Okta, Entra, CyberArk, and Active Directory — unifying identity enforcement across cloud and on-prem systems.
What authentication methods are supported offline?
Users can authenticate with CAC/PIV cards, RFID badges, passkeys, biometrics, or local credentials stored securely on the device — even with no internet.
Can organizations customize access policies locally?
Yes. Policies like role-based access control, MFA enforcement, and device posture checks can be configured and enforced at the edge without connectivity.
What failover options are available?
Credenti AlwaysON supports multiple failover paths to ensure continuous access. These include:
- Failover from your cloud IdP to an on-premises IdP (Credenti IdP).
- Failover between cloud IdPs — for example, from Entra to Okta or to Credenti IdP.
- Failover from Okta, Entra, CyberArk, or others to on-prem Active Directory (AD).
- Automatic detection and seamless transition to the next available identity source during outages.
What happens when connectivity is restored?
The platform automatically restores connectivity to the primary identity provider (IdP) configured in the platform, ensuring a smooth transition back to normal operations without user disruption.
Ready to secure your mission-critical environments?
See how Credenti AlwaysON can deliver trusted access even in your most disconnected or regulated deployments.







